Martin Cooper, right, invented the first mobile phone while working for Motorola in the 1970s. Last month, he said that continued innovation will revolutionize healthcare, education and global poverty.
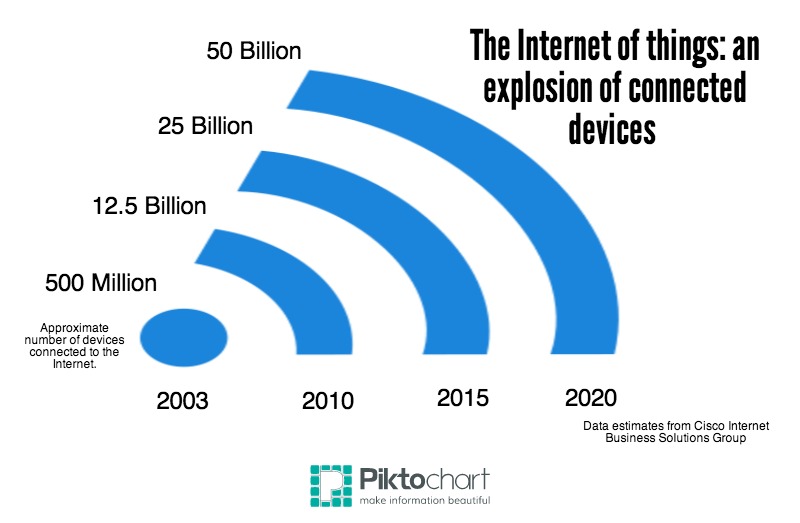
WASHINGTON — Fifty billion devices will be connected to either a network or the Internet by the year 2020, according to projections from Cisco Systems, a corporation that designs, makes and sells computer-networking devices.
That comes to about seven devices per person. Many of these devices will share information with each other via tiny sensors that collect data like sound, light and motion. This concept is known as the Internet of Things.
In a post last year for Quartz, a digital news outlet, technology reporter Christopher Mims noted that the sensors used by connected devices turn out to be very much like human senses. “Once our possessions can both sense and respond, and are directed for the most part by computers, the world becomes something like a living creature,” he wrote.
The interconnected living creature Mims describes could make life easier for countless people, but it comes with some drawbacks. The Internet of Things will contain bits of information about its user’s life that could be used to paint a pretty clear picture of his or her day-to-day experience, a picture that could be used by companies to target advertisements or by hackers bent on stealing information.
Worse, it’s possible that a person who wants to show off his or her skills could hack into your smart toaster, causing it to start a fire when it knows an owner is not home.
These innovations raise “considerable questions about how our framework for privacy protection applies in a big data ecosystem,” wrote the authors of a White House report released May 1.
Officials say that it’s critical for inventors to install security provisions into products during design phase.
“It is up to the companies that take part in this ecosystem to embrace their role as stewards of the consumer data they collect and use,” said Edith Ramirez, chairwoman of the Federal Trade Commission, at a workshop on the Internet of Things last November.
And experts agree. Frank Painter, a health care technology consultant for Technology Solutions Management, a computer consulting company, said, “Good designers can build good, safe secure designs in the first place, pretty simply, so if they did that it would preclude somebody from doing something bad.”
Among the most immediate threats to consumer safety from network connected devices are hospitals and healthcare clinics. The sheer number of products on the market calls into question the ability of government agencies to regulate them.
“There are so many different kinds of inventions and devices doing so many different things, the FDA really can’t legislate down to the line and code of security for every situation,” Painter said.
Ramirez, however, said that the agency she chairs will do what it can. “The FTC is particularly vigilant when it comes to safeguarding sensitive consumer data, such as health information,” Ramirez said. “I highlight the importance the FTC places on health information because of the numerous devices gathering this data.”
Outside of health care, the number of Internet or network devices continues to expand at a breathtaking rate. Every day 30,000 new apps are added to the market, said Deepti Rohatgi, a policy advisor at Lookout, a mobile security firm in San Francisco.
The way that Google rolled out its trial edition of Glass could serve as a model for companies that make connected devices.
Glass’ trial run gave developers a chance to test the product before it really hit the market, allowing them to point out potential vulnerabilities. Rohatgi said that Lookout employees were one group that reported a problem to Google.
“That’s a great example of how they were willing to share their technology with a group of hackers to say, ‘Help us find what the problems are before they’re released to the public,’” Rohatgi said.
And whether cooperation takes place between designers and hackers, Ramirez said that the FTC is paying close attention.
“Any device connected to the Internet is potentially vulnerable to hijack and companies need to build security into their products, no exceptions,” she said. “Companies that don’t pay attention to their security practice may find that the FTC will.”
“We are at the dawn of the Internet of Things. And like all dawns, the first light of the new day both illuminates and casts shadows.”