WASHINGTON– The term darknet conjures up scary images of a place where the darkest, most dubious members of the World Wide Web go to practice illicit activities. But the darknet and programs like Tor that allow for hidden sites and anonymous browsing help those online evade an online presence looking over their shoulders.
Despite many attempts, Tor has not been able to be cracked in a meaningful way and governments have not been able to successfully deanonymize Tor users. With the only alternative being to ban the program, which in itself is difficult, government agencies are attempting to index and track the growing activity on the darknet.
“Like everything else, Tor is a tool and tools are neutral,” said Paul Rosenzweig, a cybersecurity consultant and a former Homeland Security deputy assistant secretary in the Bush administration. “You can either throw the baby out with the bathwater and ban the tool or find some way to regulate it.”
What is the darknet and tor?
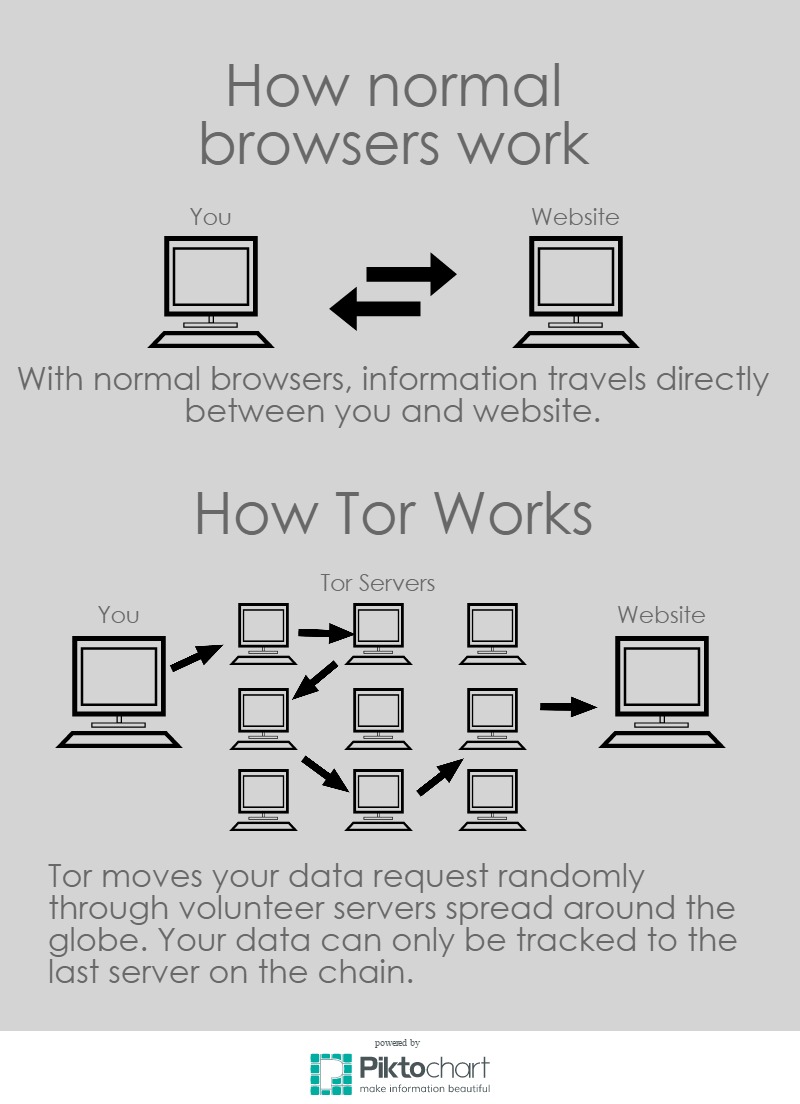 To understand the darknet, one must first understand the surface web and the deep web.
To understand the darknet, one must first understand the surface web and the deep web.
The surface web is everything that can be accessed through a search engine such as Google. This consists of basic websites that have their pages indexed and accessible to the public.
The deep web is everything that cannot be accessed by a search engine. This includes private content blocked by a login requirement or unindexed pages on a forum. It is estimated that the deep web is far larger than the surface web.
The darknet consists of sites that are intentionally hidden and can only be accessed through the use of encrypted browsers like Tor. These sites can host drug and firearm marketplaces or child pornography. More benignly, you can find hidden message boards where journalists and political dissidents from oppressed countries can communicate.
“Tor helps people be activists by giving them the anonymity they might need,” said Cooper Quintin, a technologist at the Electronic Frontier Foundation, a digital civil rights advocacy group. “Speaking out against the power structures could be a very dangerous proposition.”
Tor is an acronym that stands for The Onion Router. Onion routing was developed in the 1990s by the Navy in order to secure military communication. The code for Tor was released free to the public in 2004 and thus the darknet was born.
Today Tor receives 80 percent of its funding from the Defense Advanced Research Projects Agency.
It works by maintaining a network of volunteer servers around the world. Normally when accessing a web page, you connect directly to the server you are trying to access. Tor instead bounces your request randomly around through its scattered servers before finally reaching the desired site.
On top of that, Tor encrypts your communications when entering the Tor network and then unencrypts it on the way out. It also strips away part of the information you send out that includes identifiable information. Each stop on your request’s path through the network only unencrypts enough information to see the location of the previous stop in order to know where to send it next. These layers of encryptions allude to an onion where Tor gets its name.
How to access the Darknet
Accessing the darknet is surprisingly easy. Downloading Tor is as easy as downloading other browsers such Google Chrome and Mozilla Firefox. Darknet web addresses can be found through a simple google search.
Hiddenwiki.org provides an extensive list of darknet .onion sites that provide services ranging from renting a hacker to hiring a hitman. It is hard to know how many of these sites are simply law enforcement sting operations without actually purchasing the services. The ease of access of some of these sites makes the legitimacy of the services dubious.
 The Agora Marketplace has become the successor to the now defunct online drug marketplace Silk Road. Sites like Agora gives users a sense of reassurance based on a user’s seller rating. If a seller has a high rating, one can assume that he or she has had many successful transactions and can be trusted. It also makes it harder for law enforcement to set up a sting operations before building up their rating.
The Agora Marketplace has become the successor to the now defunct online drug marketplace Silk Road. Sites like Agora gives users a sense of reassurance based on a user’s seller rating. If a seller has a high rating, one can assume that he or she has had many successful transactions and can be trusted. It also makes it harder for law enforcement to set up a sting operations before building up their rating.
The currency used for these services are called bitcoins, an encrypted currency bought and sold over the internet and unregulated by any banking authority. Transfer of bitcoins are completely anonymous, making them the perfect currency for the darknet.
The current price of one bitcoin is about $290 but fluctuates often.
Taking stock of traffic on Tor
Researchers have been able to study traffic on Tor by setting up their own Tor servers and analyzing the traffic sent through them. They cannot find specific information on Tor users but by analyzing keywords in the data they can generally make assumptions to what kind of sites traffic is heading.
A study done by Gareth Owen at the University of Portsmouth in the United Kingdom concluded that about 80 percent of traffic moving through their Tor servers were heading towards sites pertaining to child abuse.
This finding does not necessarily prove that Tor is primarily used for child pornography because there is no way to know why each user is visiting the site.
“They could be law enforcement, they could be researchers, they could be bots just scanning the Tor hidden services,” Quentin said. “There’s no way to tell.”
More positive research on the uses of Tor comes from Eric Jardine at the Centre for International Governance Innovation. He was able to find a correlation between the oppressiveness of a country’s government and the amount of its Tor users in the country.
“People are using Tor because they lack political rights, but they are also using Tor for evil purposes,” Jardine said.
Reigning in the Darknet
Policing the Darknet is actually quite difficult because the technology behind Tor has not been cracked by any spy agency or government. There are a few methods for policing Tor users but they can only work on some of the users, some of the time.
“The cryptology behind Tor is pretty solid and it’s unlikely that the NSA would be able to crack it,” Quentin said.
There are a few methods to police darknet activity but none can effectively regulate the darknet on a grand scale.
The simplest way is for law enforcement to set up sting operations. They can either create their own hidden website or create an account on an existing one and conduct an illegal transaction. If a buyer is purchasing a physical item, an address must be given and law enforcement can simply arrive at the buyer’s doorstep once the package arrives.
It is much more difficult to arrest the people that host some of these illegal sites. The only reason why Ross Ulbricht, the founder of Silk Road, was arrested was because he was found discussing Silk Road on an Internet forum with an account linked to his actual email address.
Timing correlation attacks are a less effective way used by law enforcement to track Tor users. The process works by looking at the time a request moves through the initial server and matching it with the time a request moves out the final server and towards the hidden site. One could reasonably assume if the times match up that a specific user was accessing a specific site.
Although this method may be able to track the online movements of a few tor users, it is a long way off from effectively breaking tor.
“There is technological barriers to their ability to effectively police the darknet,” Jardine said. “The ability to directly track IP addresses doesn’t exist at this time.”
Conclusion
Tor and the darknet can be used in an increasing number of ways as concerns about the sanctity of online privacy grow.
“Whether the net benefits outweigh the costs depends on one’s perspective,” Jardine said. “In a liberal democracy it is hard to argue that a technology with a dual use can be banned just because one of those uses is criminal.”





