WASHINGTON — Bitcoin lacks the anonymity that many users have come to expect and desire, especially for a currency advertised as “cash for the Internet.”
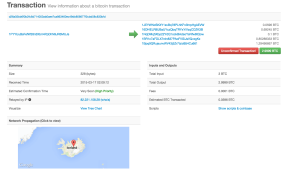
All transactions made using the online currency is logged in a public ledger to ensure their validity.
“It’s inherent in the system to have it be transparent,” said Jim Harper, a senior fellow at the libertarian Cato Institute and a member of the board of directors at the Bitcoin Foundation. “You could have greater privacy if it was a system that one party controlled, but that would have costs relying on that party to get it right.”
Bitcoin is a digital currency that has no central authority and can be used, in many ways, like cash. Many businesses, from restaurants to WordPress, have begun to accept bitcoin as payment. To get started, it only takes a few minutes to go online to set up a Bitcoin wallet.
“It is fast and free,” said David Barrett, the CEO of Expensify, a company that supports Bitcoin use for international transactions. “It’s secure. And I would say it works everywhere in the world. And it is a very powerful technology for moving money around the world.”
Bitcoin offers an “acceptable level of privacy,” according to Bitcoin.org, which is managed by its developers. And for many Bitcoin users, any potential loss of privacy is an acceptable trade-off to circumvent traditional financial institutions.
“The idea of having this flexible payment system where you can pay someone on the other side of the world without having to turn to Western Union or something, that is quite an appealing concept,” said Sarah Meiklejohn, a lecturer at University College London who has done research on the currency.
Because this cybercurrency is not tied to any country or bank, it can be a relatively stable option for those in developing countries, where the local currency is often unreliable.
But, because of Bitcoin’s transparency, it is relatively easy to track a user’s entire transaction history. The public ledger shows the location of the Bitcoin user who is making a transaction as well as the history of the Bitcoin they are spending.
“It is kind of anonymous, but the second that you do any transaction with Bitcoin, every transaction is there,” said Barrett. “Once you pay me a bitcoin, basically I can look at the log and see every transaction you’ve made.”
Bitcoin.org claims no responsibility for any “losses, damages or claims,” for invasions of privacy or thefts, according to its terms and conditions. It suggests encrypting Bitcoin wallets and using secure connections to avoid thefts.
There are ways to improve the anonymity of the currency, but they require a concerted and technology-intensive effort that many do not even know is an option.
“There’s a thing called mixing, which is a process where you commingle your bitcoins with the bitcoins of others and the output of those transactions is harder to trace back to individuals,” said Harper, the Cato fellow. “It might make it a probabilistic calculation rather than drawing a direct line.”
This process is the equivalent to moving funds through banks in countries like the Cayman Islands and Panama which have strict bank-secrecy laws.
Today, some experts are cautious in accepting Bitcoin as a widespread currency. However, many see the Bitcoin concept as one that will remain.
“It’s actually a good alternative to a currency if there is inflation,” Barrett said. “In Venezuela and Africa, it is getting larger adoption. Russia also has a big growth in bitcoin. It’s a safer and less volatile way to keep your currency. Over time, Bitcoin will, in certain parts of the world, become a daily occurrence.”
Bitcoin and its supposed anonymity gained prominence in its role with the Silk Road, an online black marketplace known for selling illicit drugs and weapons. Buyers and sellers were able to connect virtually and use the cybercurrency to conduct anonymous transactions.
“This perception of anonymity might be driving groups towards Bitcoin, but then the transparency is giving law enforcement or anyone interested in these illicit transactions this beautiful view of all of these types of illicit transactions,” said Meiklejohn, the Bitcoin researcher. “Instead of going to somewhere like Western Union and wiring cash over to the Islamic State or whatever, if you’re doing it with Bitcoin then you are creating this paper trail that is never going to go away, literally ever.”
What may scare off more potential Bitcoin users, however, is not its lack of anonymity, it’s the volatility of the currency. In the last 12 months, the value of the currency has fallen by nearly half.
“Maybe I’m just cynical, but it’s hard to see why Bitcoin, as it is now, would achieve widespread adoption, which ultimately is what you would need to have any kind of stable currency,” Meiklejohn said. “So, as long as Bitcoin is this niche market, it is going to remain pretty volatile.”